Printers at several colleges and universities around the world were abused to print racist and anti-Semitic messages. The print jobs were submitted remotely, exploiting open network ports and lax firewall settings. The incident highlighted how open printer networks can be used as conduits for malicious activity.
Printers: The Original “Internet of Things” Device
Printers often present information technology teams with unique challenges. Their maintenance demands—toner, paper, jam clearing—can encourage a “set-and-forget” approach. Most enterprise printers work out of the box, so technical staff may not prioritize setting up strong device passwords, configuring internal firewalls, or requesting secure network segments. As a result, printers frequently become the most widely deployed—and least secured—“Internet of Things” devices within organizational networks.
IT staff and decision-makers, often focused on operational efficiency, may not imagine that printers could be exploited beyond their intended use. Yet, recent incidents demonstrate that these devices are highly vulnerable targets.
Exposed & Open Ports
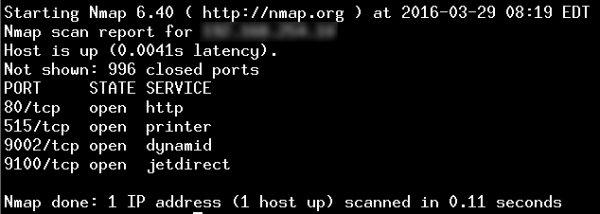
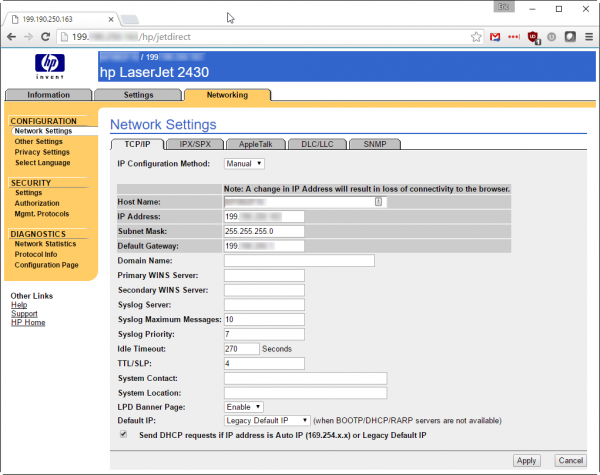
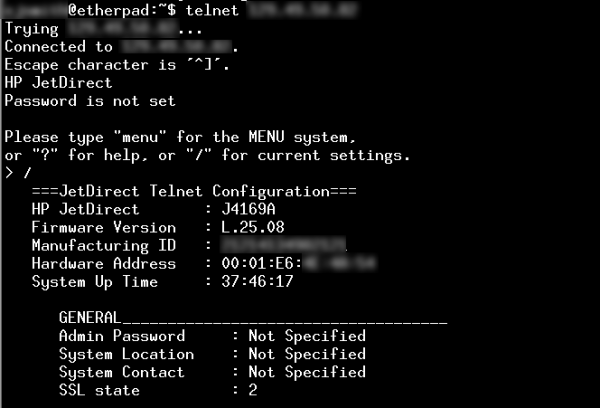
A quick scan using security tools can reveal tens of thousands of US-based printers with their TCP port 9100 (“jetdirect”) exposed directly to the internet. This port enables the receipt of print jobs and device management. Many printers also expose older protocols (such as TCP port 515 for “lpd”) and administrative interfaces—both web-based and via command-line (telnet). Coupled with weak or default passwords, this creates an easy entry point for attackers.
Why Printers Should Be Segmented
- With access to exposed printer ports, attackers can disrupt service, intercept confidential print jobs, store files, or even upload malicious software.
- Determined adversaries might leverage the computing power of internet-connected printers to launch additional attacks against organizational assets.
- Because printers are often anchored within core networks, this puts sensitive information and infrastructure at risk.
Proper Segmentation: An Essential Security Practice
Network segmentation—filtering traffic within and between functional areas—dramatically reduces an organization’s risk exposure, even if some devices remain improperly configured. As the proliferation of IoT devices continues, strong segmentation, robust network access controls, and device-level authentication are essential components of operational clarity and a resilient information security program. These measures help ensure that mission-driven organizations can protect their knowledge assets and maintain operational continuity in an evolving threat landscape.
Read more:






