On March 24, 2016 printers at several colleges and universities around the world were used to print racist and anti-Semitic messages. The print jobs were submitted remotely, taking advantage of unsegmented, open network ports and overly-permissive firewall settings. This open architecture was exploited, allowing the printers to be used as a conduit for the delivery of hate speech.
Printers: The Original “Internet of Things” Device
Printers tend to be the bane of information technology staff everywhere. The constant care and feeding required — changing toner, loading paper, clearing jams — tends to promote a “keep it simple” mindset among IT staff. Most enterprise-grade network-attached printers simply work as-is out of the box as soon as they are plugged into the network. There is little perceived benefit for technical staff to spend time setting device passwords, configuring units’ built-in firewalls, or asking a network team to activate a new port on the the secure printing network. This all-too-common approach allows printers to assume a rather unusual posture in the enterprise network: they are the most widely-deployed “Internet of Things” devices in every organization, are connected to the core of the enterprise network, and are only rarely properly secured.
IT staff members or executives often don’t feel the need to apply typical best practices to these devices, leaving printers on unsegmented networks and leaving ports open and exposed — usually because decision-makers, who are focused on streamlining business operations, exhibit a lack of imagination regarding how printers could be used in unintended and malicious ways. But as this week’s series of events demonstrates, printers are highly exploitable.
Exposed & Open Ports
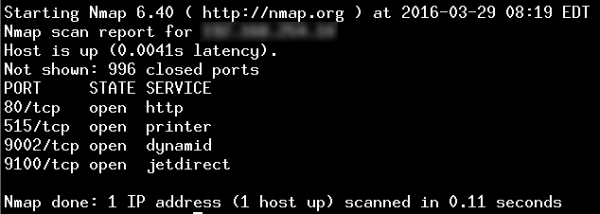
A quick Shodan search identifies over 78,000 US-based printers with their TCP port 9100 directly connected to the internet. Port 9100, sometimes referred to as the “jetdirect” port, is typically used by printers to receive print jobs and perform other management functions. In addition, many of these devices have TCP port 515 (the older “lpd” printing protocol) exposed as well, suggesting that there are no firewalls, packet-filtering routers, or intrusion prevention systems in place at the local network where the printers reside.
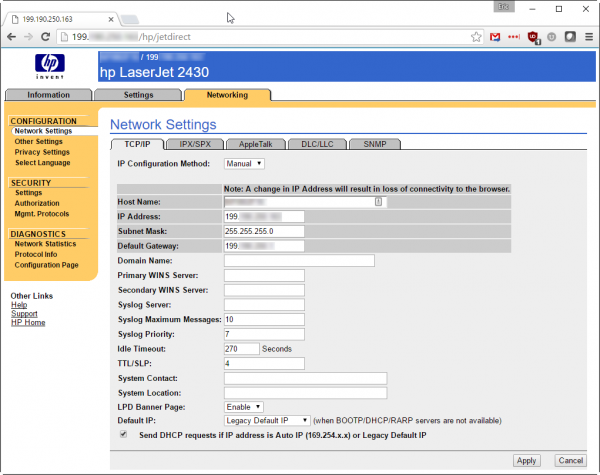
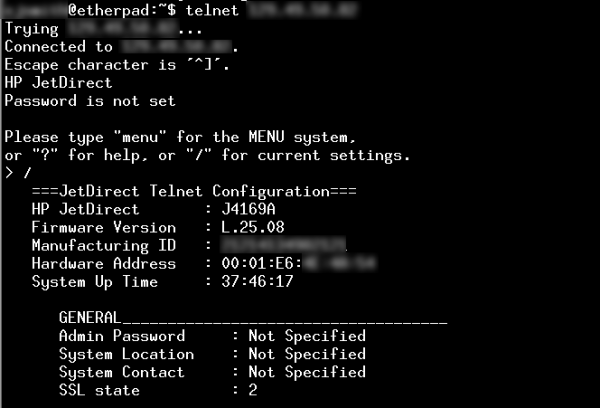
If the exposed jetdirect port isn’t damaging enough, many printers also expose their administrative interfaces — both command-line telnet and web-based tools — to the internet. Combined with missing, weak, or default passwords, this allows attackers easy access to device configurations.
Why Printers Should be Segmented
Armed with such access, an attacker could easily take a printer out of service, intercept confidential print jobs, store files, or even upload malicious software to the printer. A less-determined attacker could, of course, simply use the device as intended and send a document to be printed.
Determined adversaries can use the computing power of the printer itself to launch subsequent attacks against other critical assets within the organization. Since printers are usually positioned within the core of the enterprise network, such attacks can be devastatingly effective.
Proper Segmentation: An Essential Security Practice
Proper network segmentation is achieved by filtering traffic into and out of the various functional areas of an organization’s network. Even if unsecured printers continue to be deployed within the enterprise network, a properly-segmented network drastically reduces the attack surface and mitigates most of the attacks highlighted here. The Internet of Things (IoT) phenomenon is not going away, and it is unrealistic to expect that policies alone will prevent unconfigured IoT devices from being connected to the enterprise network. Strong segmentation, robust network access controls, and port-level authentication are just a few of the components of a strong information security program that are key to mitigating these and many other types of attacks against the organization’s information assets.






