For years, FireOak has been recommending to clients that they implement an enterprise password management platform as part of their cybersecurity strategy. FireOak is not a reseller of any platforms, but increasingly we’ve been recommending Bitwarden for organizations that are in the market for a new enterprise password management platform. Bitwarden is easy to deploy, but it does contain several enterprise-level settings that must be configured and fine-tuned to align with other security policies. Following are FireOak’s recommended Bitwarden settings. All of these settings require admin permissions and can be accessed through Bitwarden’s web interface via “Organizations > Settings > Policies.”
Overview of FireOak’s Recommended Bitwarden Settings
- Two-step login (MFA): Required
- Master password requirements:
- Minimum complexity score = Strong (4)
- Minimum length = 20
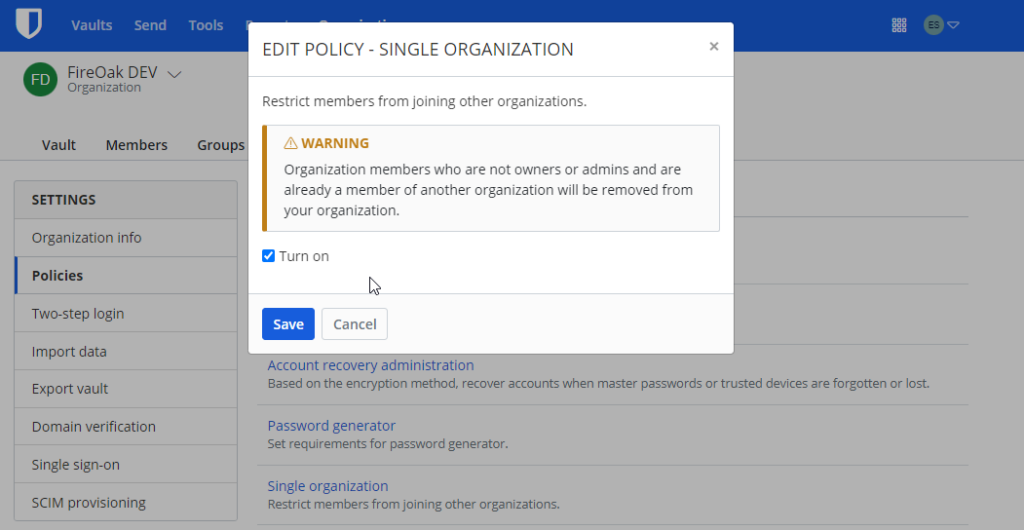
- Single organization policy: turn on
- Account recovery administration: turn on
- Remove individual vault export: turn on
Continue reading for more details about each of these recommended Bitwarden settings.
Multi-Factor Authentication
Bitwarden refers to multi-factor authentication (MFA) as “two-step login.” It is imperative that all users rely on multi-factor authentication wherever and whenever it is possible, starting with their password manager. To avoid having any gaps, we recommend requiring all users to set up MFA for Bitwarden.
Master Password Requirements
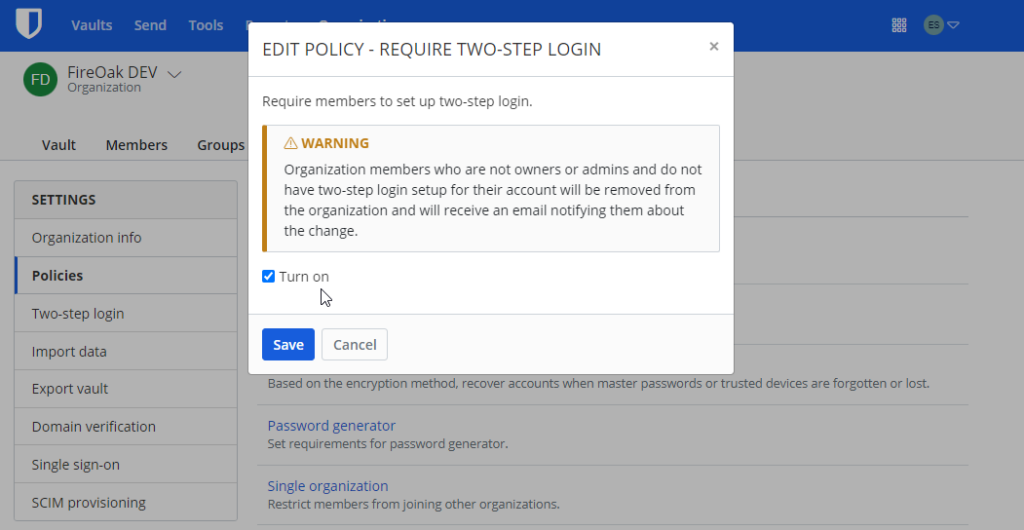
Each user has a “master password” within Bitwarden that is used to log into Bitwarden. It is critical that this master password follows current best practices. We recommend setting the requirements for master password strength as follows:
- Turn on this setting
- Require existing members to change their passwords so they are brought into compliance with the new policy
- Setting the minimum complexity score to “Strong (4)”
- Setting the minimum length to 20 characters
This format lends itself to the use of passphrases rather than passwords, which is a far more secure approach.
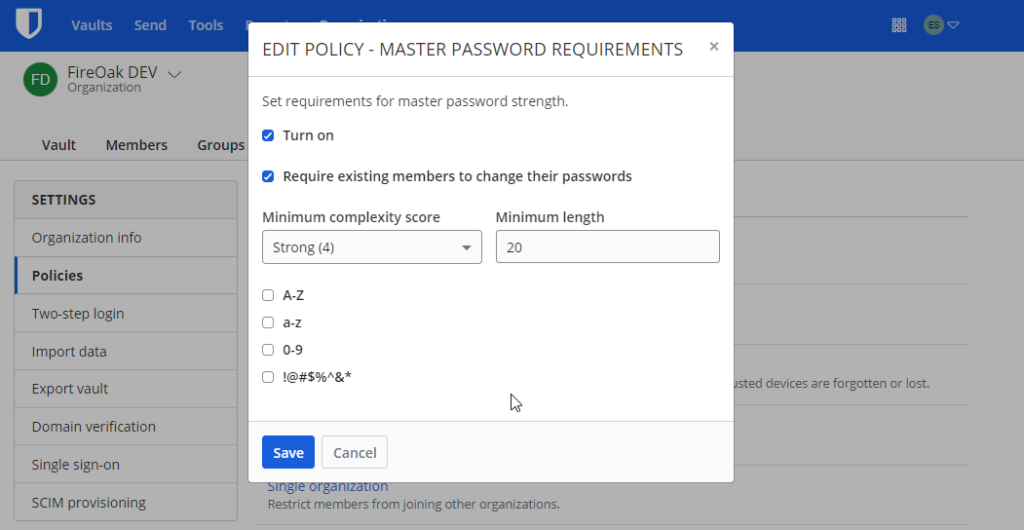
Single Organization Setting
The “single organization” setting is important as it is necessary as it is a prerequisite for enabling account recovery administration (see next section).
However, by turning on the policy for “Single Organization,” users who are not owners or admins and are already a member of another organization will be removed from the organization. Users will receive an email about this change, and then they will need to remove themselves from other organizations before they can re-join your organization.
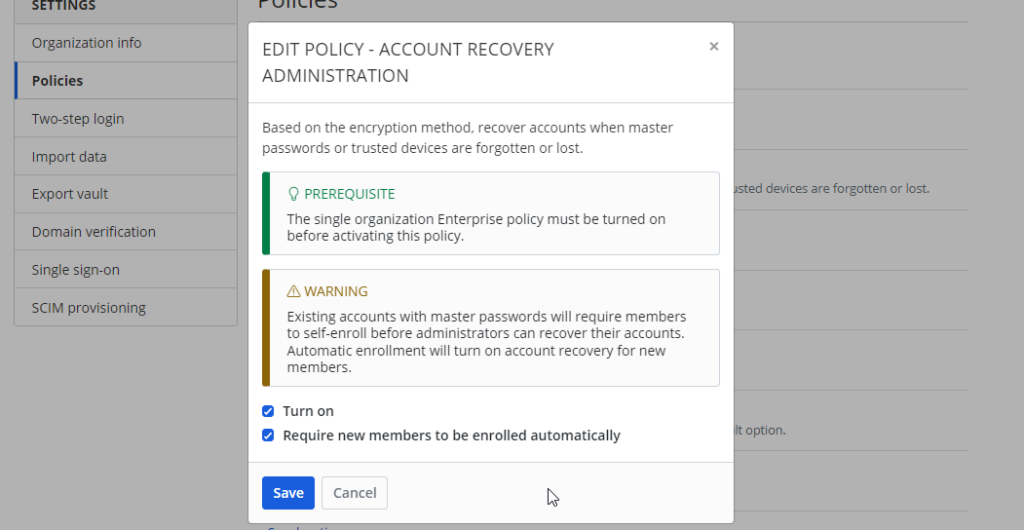
Account Recovery Administration
For an enterprise deployment, having account recovery administration turned on will be a huge help for your IT help desk. When staff members go on extended leave, they often forget their passwords, including their passwords for their password management tool. Having a mechanism in place for the IT help desk to be able to reset a password is a big win.
Vault Exports
The last of FireOak’s recommended Bitwarden settings is to disable individual users’ ability to export their vault data. This setting will prohibit users who aren’t owners or admins from exporting their data.
Words of Caution When Implementing Enterprise Policy Settings
The best time to implement these changes is before opening up Bitwarden for enterprise adoption. However, if your organization has already deployed Bitwarden and you’re trying to retroactively enhance security measures, you’ll need to do some extra planning and figure out the best course of action for your organization as some of these changes have impacts for existing users.
Pay attention to the warning messages in the Bitwarden settings to understand the implications of making changes that will impact existing users. For example, when changing the setting to require two-step login (MFA):
“Organization members who are not owners or admins and do not have two-step login setup for their account will be removed from the organization and will receive an email notifying them about the change.”
If your organization only has a few users, it might be best to coordinate with each of them before implementing the organization-wide policy. However, if Bitwarden was rolled enterprise wide, it might be necessary to take a different approach. But in either case, getting this setting enabled is critical.
Conclusion
Bitwarden is a great tool, but there are several recommended Bitwarden settings that we strongly recommend enabling for enterprise accounts. Without changing these settings at an enterprise level, users – even well-intentioned ones – will stick to defaults and won’t implement many of the important controls that are designed to protect organizational information, data, and knowledge. If at all possible, we recommend implementing these enterprise policies before onboarding new users for your organization. If it’s too late for that, it will require an additional level of change management, communication, and coordination with users. But even so, the extra layers of protection are worth it.
Need help with an enterprise Bitwarden deployment? Contact the FireOak team for help.






